The Cisco Identity Services Engine (ISE) is simple policy (endpoint, node) enforcement platform. It has a dynamic and automated approach to authentication and authorization of ‘network access’ across both wired and wireless networks… the second you plug into switchport or click “join this network” respectively.
From 1 to 1000’s of employees, 1 to 1000’s of customers coming in and out of your business daily… visitors, contractors, consultants, and customers… whatever it may be.
For wireless:
Get a Wireless LAN Controller (WLC) and some WAP’s or a LINKSYS WR and manage them that way, right?
Here’s is the SSID & Passphrase or Here’s the username and password.
For wired:
switchport mode access
switchport access Vlan 100
And now full access to the network! Let the company’s ‘stuff’ take care of the rest. Shared, borrowed, stolen connections into your network are never good.
But let’s forget that for now… Users will use your network. They will come and go. This is how all the big dogs do it… those users didn’t matter! They didn’t want to know who? What? When? Where? and how? NOT!!!
For example, ISE provides you… a new wireless user (now getting an email from the guest sign-in – for a company newsletter, etc), the time and location of the request (lows and highs), as well the access method (wired or wireless) and the type of device (smartphone & watch, tablet, laptop, computer – IOT) used.
Once the request to your network is legitimate, only then can the user gain access to the network. First, allow/send them to the company website, guest portals, wiki, forums, etc. or maybe that’s good enough? Deny/drop YouTubeTV and/or AppleTV.
NO more are the days of “Welcome to @FULL access to my network!”
So, reading from above our wireless industry has been on the band wagon since version one with the wired environments not far behind. It provides excellent benefits for its customers that adopt it. With these controls integrated and/or designed within a Cisco network, you’ll be able to identify and manage access, address/remediate against cyber threats, and make it easy to enforce ethical business conduct and to meet monthly or quarterly organization security audits and/or policies. Cisco ISE aims to give all companies compliance with corporate security policies or policies levels. Complying with ever-changing regulations should never be a worry.
Cisco ISE will provide automation, timesaving, cost-saving, top-level security, increased visibility, and control. The control that will limit threats, increase end user visibility, and provide secure access to network resources. There is no better commercial NAC product than Cisco ISE!
Highlights
- Gain visibility with context and control: Know who, what, where, and how endpoints and devices are connecting to your network to ensure compliance and limit risk, with or without the use of agents.
- Extend zero trust to contain threats: Software-Defined Network segmentation shrinks the attack surface, limits the spread of ransomware, and enables rapid threat containment.
- Accelerate the value of existing solutions: Integrate with other Cisco and third-party solutions to bring an active arm of protection into passive security solutions and increase your return on investment (ROI).
Key Functions
Cisco ISE is a consolidated policy-based access control system that incorporates a superset of features available in existing Cisco policy platforms. Cisco ISE performs the following functions:
• Combines authentication, authorization, accounting (AAA), posture, and profiler into one appliance
• Provides for comprehensive guest access management for Cisco ISE administrators, sanctioned sponsor administrators, or both
• Enforces endpoint compliance by providing comprehensive client provisioning measures and assessing
the device posture for all endpoints that access the network, including 802.1X environments
• Provides support for discovery, profiling, policy-based placement, and monitoring of endpoint devices on the network
• Enables consistent policy in centralized and distributed deployments that allows services to be delivered where they are needed
• Employs advanced enforcement capabilities including Trustsec through the use of Security Group Tags (SGTs) and Security Group Access Control Lists (SGACLs)
• Supports scalability to support a number of deployment scenarios from small office to large enterprise environments Identity-Based Network Access
The Cisco ISE solution provides context-aware identity management in the following areas:
• Cisco ISE determines whether users are accessing the network on an authorized, policy-compliant device.
• Cisco ISE establishes user identity, location, and access history, which can be used for compliance and reporting.
• Cisco ISE assigns services based on the assigned user role, group, and associated policy (job role, location, device type, and so on).
• Cisco ISE grants authenticated users with access to specific segments of the network, or specific applications and services, or both, based on authentication results.
PROOF OF CONCEPT
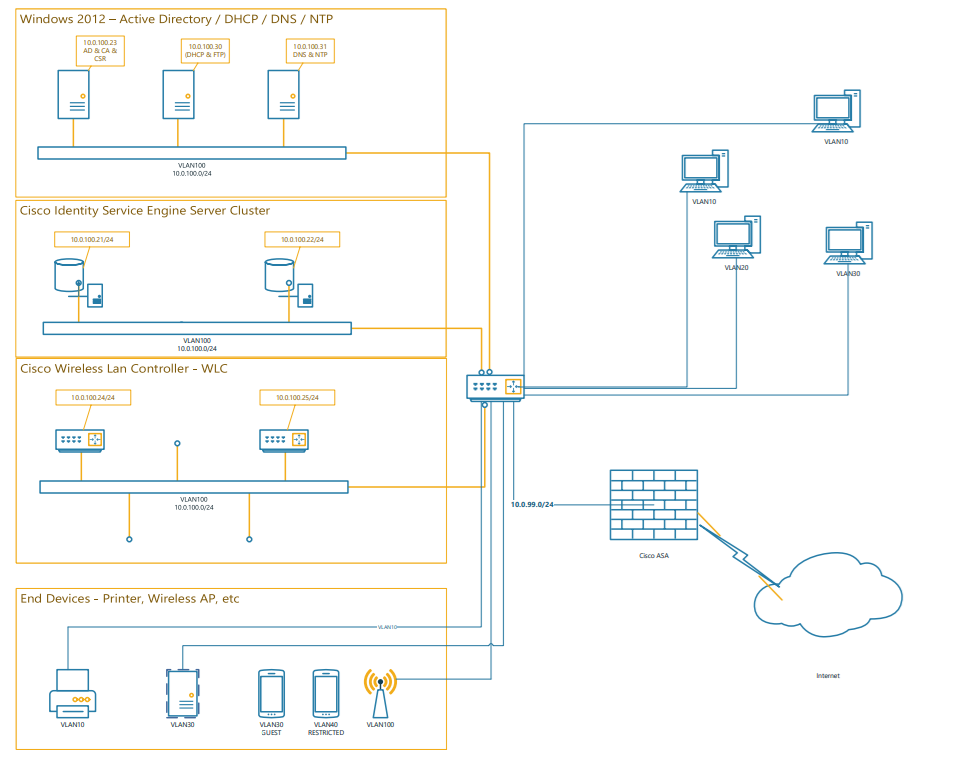
Design, configure, and deployment of Cisco Identity Services Engine (ISE) v.3 within a Microsoft Windows Active Directory – TACACS+ & RADIUS. 802.1x & Mac (MAB) Authentication & Authorization for Wired & Wireless (Router, Switch, FW and WLC) – network and appliance.
- Configuration/Establishment & integration of Certification Stores, Authentication & Authorization between Cisco ISE and MS Active Directory & Certificate Authority. PEAP, MSCHAPv1, MSCHAPv2 and EAP-TLS
- Implement redundant/HA ISE solution
- Integrate and establish TACACS (AA profile & policies, command sets, shell profiles, conditions) services for Network device administration with internal and MS AD stores within Cisco ISE.
- Implemented and documented a custom fully redundant and Highly Available WLAN environment utilizing 550x Wireless LAN Controllers, 33xx ISE Appliances, and Wireless Access Points of 11xx, 350x and 360x series.
- Design, migrate, deploy, configuration and administration of virtualization of Cisco ISE Servers with VMWARE ESXi and/or VM Server/workstation (platform and networking).
- Create the repository for the backup and performing upgrades.
WIRELESS & WIRED: How we have our end devices defined and configured – WIN SUPPLICANT – TEAP w/ EAP-TLS & Chaining – USER and/or MACHINE & Posture (AnyConnect module) and MS GROUP
IoT/BOYD: DIGITAL SIGNAGE, CAMERA, PRINTER, PHONES:
- DIGITAL SIGNAGE – MAB by Profiling – Conditions specified by MAC for OEM space, Expressions MAC:MACaddress contains “OEM/Vendor” identifier” (can be by IP, SNMP, Radius, etc)
- CAMERA – MAB by Profiling – Conditions specified by MAC for OEM space, Expressions MAC:MACaddress contains “OEM/Vendor” identifier” (can be by IP, SNMP, Radius, etc)
- PRINTER – MAB by Profiling – created Cisco ISE conditions – MAC, OUI, Attribute value suggest moving to specific MAC
- PHONES – MAB by Profiling – created Cisco ISE conditions – MAC, OUI, Attribute value
MOCK LAB: Adding Cisco ISE (Identity Services Engine v3.0)
Purpose: AAA (TACACS or RADIUS) for WIRED or WIRELESS (BYOD, etc) & Training unlimited
Installation of:
Cisco switch(s) 3750, 3850, 9300 & 9500
Cisco firewall ASA 5510
Windows Server 2022
Cisco ISE v3.0 (ISE1 & ISE2)
Cisco WLC AIR-CT2504
Cisco WAP’s CAP11xx, 35xx, 36xx
Certificate Store – MS 2022 CA
Virtualization via ESXi and VMWARE
Updates:
12/2024 – Windows Server 2012 R2- UPGRADED to MS 2019
12/2024 – Established, configured & integration of Certificate Stores between ISEv3 and MS AD w/ MS CA.
12/2024 – Deployment of Guest AA – Guest Portal Completed – ISE_WLC_WAP w/ MAB WIRELESS – ssid: Guest-Ise
12/2024 – Deployment of Windows AD Users AA wired & wireless – for wireless ssid: VOC-Employee
12/2024 – Remote abilities for training (administration, example, testing, etc)
12/19/2024 – Added High Availability (HA) – ise1.voc.local & ise2.voc.local (Admin, Monitoring, Policy Services)
12/19/2024 – Group / Endpoint VLAN assignment (MS AD – DHCP)
- Employee VLAN10 (10.0.10.0/24)
- Contractor VLAN20 (10.0.20.0/24)
- Guest VLAN30 (10.0.30.0/24)
- Restricted/Limited VLAN40 (10.0.40.0/24)
- Core VLAN100 (10.0.100.0/24)
12/23/2024 – User-only and User & Machine w/ PAP (MS-Chap v1 & v2), EAP-TLS (Certificate) Authentication
12/30/2024 – Virtualization of ISE1, ISE2 and Windows 2019 Server – ESXi
1/1/2025 – Switch’s configuration change to IBNS 2.0
1/2/2025 – Configured TACACS+ via Cisco ISE. Internal and/or MS AD authorize and authentication. Configured network devices for access – Gateway/Switch 10.0.100.1 – use Microsoft AD account – SSH & Telnet both accepted
1/13/2025 – ISE Failover and unavailability – End node access through Policy & Service Control – Switch configuration updated (putty_switch_3750.txt)
1/25/2025 – Configured TACACS w/ MS AD Network Groups – IT_RW_NETWORK and IT_RO_NETWORK – Applied Command Authentication & Authorization (Gateway/Switch 10.0.100.1 – use Microsoft AD account – SSH & Telnet both accepted)
2/14/2025 – Windows Server 2019- UPGRADED to MS 2022
3/24/2025 – Deployed Cisco ISE 3.1 in AWS – Identity Services Engine (https://ec2-44-198-52-19.compute-1.amazonaws.com/admin/login.jsp)
| ISE 3.1 P1 AMI-bedef662-aba4-427e-b523-7c93cd50111c (ami-0bb0a9d243824a077) | |
| Description [ami-0426d05e48c1feb2c from ap-south-1] | |
| Status: available | |
| Platform: Other Linux | |
| Image Size: 300GB | |
| Visibility: Public | |
| Owner: Voc.systems |
TACACS Configuration:
- Policy Set Name – BIZ TACACS
- Only Authentication Protocols relevant to TACACS are displayed.
- Allow PAP/ASCII
- Allow CHAP
- Allow MS-CHAPv1
- Rule Name: Full Admin – Conditions: EXTERNAL AD GROUP – TACACS_Full
- Rule Name: Show Only – Conditions: EXTERNAL AD GROUP – TACACS_Show
- Rule Name: Full Admin – RESULTS *COMMAND SETS: BIZ ADMIN FULL
- Rule Name: Show Only – RESULTS *COMMAND SETS: SHOW COMMAND ONLY
- Rule Name: DEFUALT – RESULTS *COMMAND SETS: DenyALLCommands
- Rule Name: Full Admin – RESULTS *SHELL PROFILE: BIZ ADMIN
- Rule Name: Show Only – RESULTS *SHELL PROFILE: TACACS SHOW
- Rule Name: DEFUALT – RESULTS *SHELL PROFILE: Deny All Shell Profile
- TACACS Command Sets
- DenyAllCommands
- BIZ ADMIN FULL – Permit any command that is not listed below
- SHOW COMMAND ONLY – Permit “exit” “ping” “traceroute” “show”
- TACACS Profiles
- Deny All Shell Profile – Type: Shell Default Shell Profile
- BIZ ADMIN – Type: Shell – default priv 15 – max priv 15
- TACACS SHOW – Type: Shell – default priv 15 – max priv 15